Announcing Twingate's Partnership with 1Password Device Trust
Emily Lehman
•
Oct 24, 2024

Twingate’s central mission is to ensure that people can work securely from anywhere. We believe that modern security challenges are best solved by adopting a Zero Trust framework, but it’s a deceptively complex framework to operationalize.
There is a reason why the concept of Zero Trust has existed for decades, but remains relatively low in terms of full adoption: simply put, it’s really hard to do. Legacy solutions, even those in the cloud, are not built for organizations with globally distributed employees and environments spanning on-prem, cloud, and SaaS applications.
Twingate is built from the ground up to help organizations take Zero Trust concepts, and put them into practice. It all comes down to a question: Should this user, on this device, in this context, access this resource?
The ability to answer that question requires comprehensive visibility into identity, devices, and access across your entire network, which is why we’re thrilled to announce our newest partnership with 1Password Device Trust. 1Password, a leader in identity security, has expanded its offerings to fill critical gaps in access management and identity by enabling businesses to secure every sign-in to every application from every device. With this new integration, you can now verify devices in Twingate using 1Password Device Trust.
Architecture Matters
One of the main reasons Zero Trust has been so burdensome to adopt is that legacy solutions come with significant gaps.
Many organizations have already moved away from VPNs due to security, administrative, and performance downsides. Cloud proxy models were introduced over 15 years ago as the first attempt to solve these, and while they solve many of the security challenges of VPNs, they introduce their own issues around performance, reliability, and administration. All of these are compounded by the complex access questions introduced by cloud adoption and the move to distributed and hybrid workforces.
This increase in distributed workforces - especially hybrid and contractor workforces - has highlighted gaps not just in network access, but also device and identity. While historically admins focused primarily on securing company-managed devices, BYOD and third-party users who use non-company devices to access internal environments pose significant risk to security and IT teams.
The new Twingate and 1Password partnership solves these challenges by closing the gaps in security and performance on the network, identity, and device layers.
Twingate’s Enterprise Peer-to-Peer architecture establishes direct connections between devices and resources so users always get a fast, low-latency connection to work resources without compromising on security. With a dual-verification process - at the device and behind the firewall - Twingate ensures that any network connection is meticulously controlled and verified. All traffic is encrypted, and your private resources remain entirely hidden from the open internet.
To strengthen that verification process further, Twingate invests heavily in first-class integrations with leading products in modern security stacks. As a central access control layer, Twingate makes it easy to bridge together the various component solutions that form your unique security stack, including major IdPs, MDMs, EDRs, SIEMs, and more to implement an access control framework based on Zero Trust..
Partners like 1Password makes it easy for admins to apply the multiple layers of security needed to implement Defense in Depth, making it harder for malicious actors to access sensitive resources.
How it works
Within 1Password, you have the ability to granularly select requirements from an extensive library of device checks. Especially important is the ability to extend these checks to every device – even for bring-your-own devices and contractors, in addition to corporate devices managed via MDM.
Both Twingate and 1Password believe that security controls that are hard to use don’t get used at all. Because of that, we designed this integration to be simple and straightforward to implement.
Select 1Password as a verification method for Trusted Devices under the Device Security tab of the Twingate Admin Console.
Create or edit a Trusted Profile for Windows, macOS, or Linux with 1Password enabled as a verification requirement
Apply this Trusted Profile on any Twingate protected resource where 1Password device verification is required
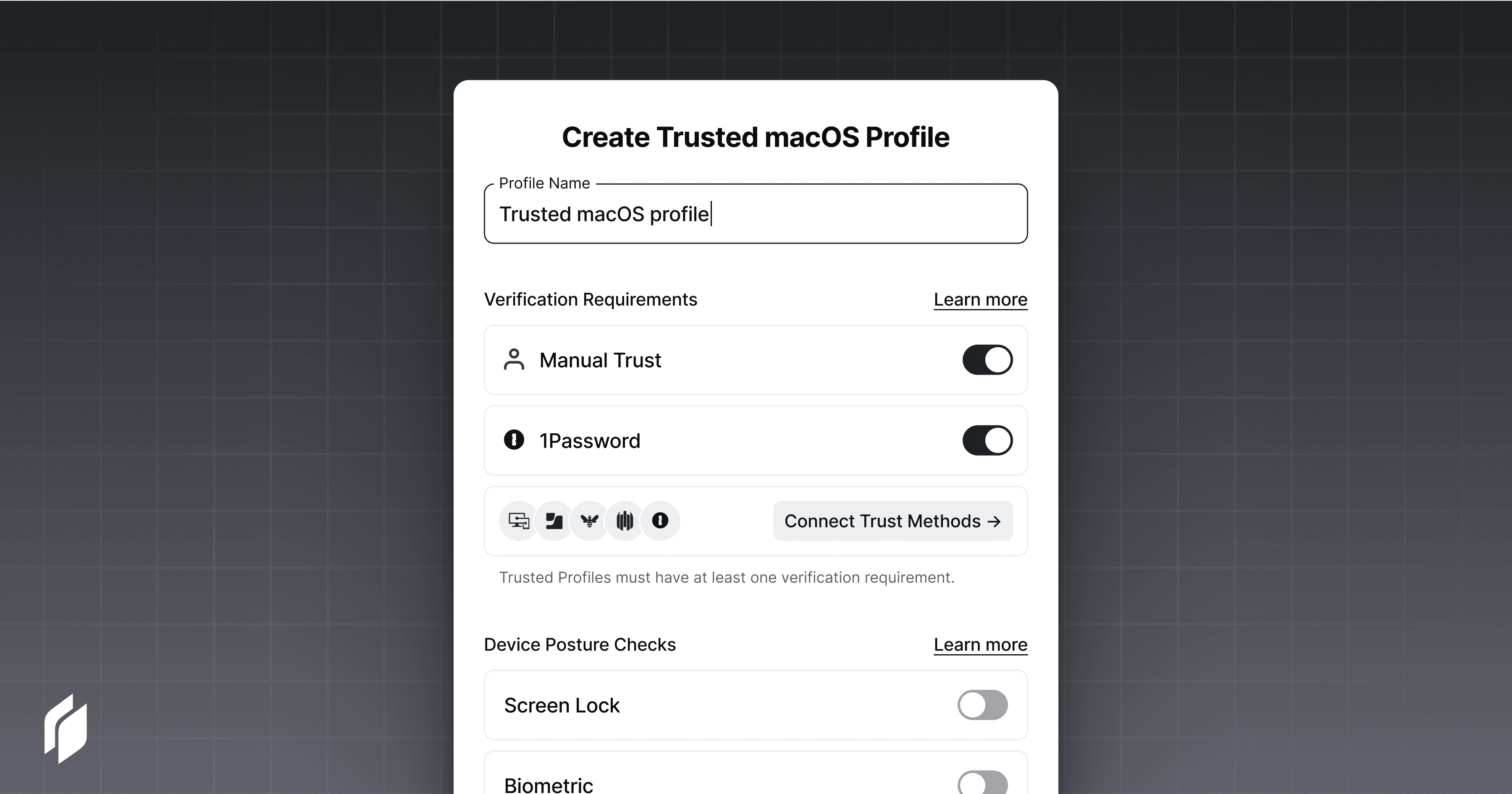
That’s it!
Bridging Security and Usability
In today’s world, end user experience is not just a “nice to have” that can be sacrificed in the name of security.
What modern organizations are increasingly realizing is that usability is actually an important consideration for stronger security. Any tool that introduces too much friction for end users can drive a number of negative outcomes.
Both Twingate and 1Password believe security and usability shouldn’t be in conflict. In fact, they should be working together: a better end user experience leads to stronger buy-in for security programs. That means delivering both powerful security controls and a seamless end user experience.
Twingate does this by using the modern network protocol QUIC and advanced networking techniques like NAT traversal to establish direct peer-to-peer connections between users and resources. This, in combination with Twingate’s flexible deployment model, allows security teams to implement security controls for even the most niche environments and workflows without slowing down the pace of development.
1Password focuses on securing the way people already intuitively work so that the easiest path for them to take is also the most secure. Because Device Trust works equally well on business and personal devices, employees are encouraged to secure their personal devices with Device Trust because that is the easiest way to access applications.
Building the Zero Trust ecosystem
At Twingate integrations aren’t just another “nice to have” feature. Despite how the market often portrays it, Zero Trust is a framework, not a single solution. That means any organization will need multiple tools in order to actually see the security benefits of a Zero Trust model in action.
And yet very few of those tools actually play nicely. We believe it’s critical to build a product that doesn’t just work with, but actually enhances the benefits of other cybersecurity tools.
Partnering with solutions like 1Password Device Trust, Twingate enables businesses to take a holistic approach to security by connecting identity, devices, and access into enforceable security programs.
We’d like to thank the 1Password team for their close collaboration on this, and we’re excited to continue investing in our technology partners!
Not a Twingate customer yet? If you’re interested in taking Twingate for a spin, you can request a personalized demo from our team or try it out yourself for free.
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Announcing Twingate's Partnership with 1Password Device Trust
Emily Lehman
•
Oct 24, 2024

Twingate’s central mission is to ensure that people can work securely from anywhere. We believe that modern security challenges are best solved by adopting a Zero Trust framework, but it’s a deceptively complex framework to operationalize.
There is a reason why the concept of Zero Trust has existed for decades, but remains relatively low in terms of full adoption: simply put, it’s really hard to do. Legacy solutions, even those in the cloud, are not built for organizations with globally distributed employees and environments spanning on-prem, cloud, and SaaS applications.
Twingate is built from the ground up to help organizations take Zero Trust concepts, and put them into practice. It all comes down to a question: Should this user, on this device, in this context, access this resource?
The ability to answer that question requires comprehensive visibility into identity, devices, and access across your entire network, which is why we’re thrilled to announce our newest partnership with 1Password Device Trust. 1Password, a leader in identity security, has expanded its offerings to fill critical gaps in access management and identity by enabling businesses to secure every sign-in to every application from every device. With this new integration, you can now verify devices in Twingate using 1Password Device Trust.
Architecture Matters
One of the main reasons Zero Trust has been so burdensome to adopt is that legacy solutions come with significant gaps.
Many organizations have already moved away from VPNs due to security, administrative, and performance downsides. Cloud proxy models were introduced over 15 years ago as the first attempt to solve these, and while they solve many of the security challenges of VPNs, they introduce their own issues around performance, reliability, and administration. All of these are compounded by the complex access questions introduced by cloud adoption and the move to distributed and hybrid workforces.
This increase in distributed workforces - especially hybrid and contractor workforces - has highlighted gaps not just in network access, but also device and identity. While historically admins focused primarily on securing company-managed devices, BYOD and third-party users who use non-company devices to access internal environments pose significant risk to security and IT teams.
The new Twingate and 1Password partnership solves these challenges by closing the gaps in security and performance on the network, identity, and device layers.
Twingate’s Enterprise Peer-to-Peer architecture establishes direct connections between devices and resources so users always get a fast, low-latency connection to work resources without compromising on security. With a dual-verification process - at the device and behind the firewall - Twingate ensures that any network connection is meticulously controlled and verified. All traffic is encrypted, and your private resources remain entirely hidden from the open internet.
To strengthen that verification process further, Twingate invests heavily in first-class integrations with leading products in modern security stacks. As a central access control layer, Twingate makes it easy to bridge together the various component solutions that form your unique security stack, including major IdPs, MDMs, EDRs, SIEMs, and more to implement an access control framework based on Zero Trust..
Partners like 1Password makes it easy for admins to apply the multiple layers of security needed to implement Defense in Depth, making it harder for malicious actors to access sensitive resources.
How it works
Within 1Password, you have the ability to granularly select requirements from an extensive library of device checks. Especially important is the ability to extend these checks to every device – even for bring-your-own devices and contractors, in addition to corporate devices managed via MDM.
Both Twingate and 1Password believe that security controls that are hard to use don’t get used at all. Because of that, we designed this integration to be simple and straightforward to implement.
Select 1Password as a verification method for Trusted Devices under the Device Security tab of the Twingate Admin Console.
Create or edit a Trusted Profile for Windows, macOS, or Linux with 1Password enabled as a verification requirement
Apply this Trusted Profile on any Twingate protected resource where 1Password device verification is required

That’s it!
Bridging Security and Usability
In today’s world, end user experience is not just a “nice to have” that can be sacrificed in the name of security.
What modern organizations are increasingly realizing is that usability is actually an important consideration for stronger security. Any tool that introduces too much friction for end users can drive a number of negative outcomes.
Both Twingate and 1Password believe security and usability shouldn’t be in conflict. In fact, they should be working together: a better end user experience leads to stronger buy-in for security programs. That means delivering both powerful security controls and a seamless end user experience.
Twingate does this by using the modern network protocol QUIC and advanced networking techniques like NAT traversal to establish direct peer-to-peer connections between users and resources. This, in combination with Twingate’s flexible deployment model, allows security teams to implement security controls for even the most niche environments and workflows without slowing down the pace of development.
1Password focuses on securing the way people already intuitively work so that the easiest path for them to take is also the most secure. Because Device Trust works equally well on business and personal devices, employees are encouraged to secure their personal devices with Device Trust because that is the easiest way to access applications.
Building the Zero Trust ecosystem
At Twingate integrations aren’t just another “nice to have” feature. Despite how the market often portrays it, Zero Trust is a framework, not a single solution. That means any organization will need multiple tools in order to actually see the security benefits of a Zero Trust model in action.
And yet very few of those tools actually play nicely. We believe it’s critical to build a product that doesn’t just work with, but actually enhances the benefits of other cybersecurity tools.
Partnering with solutions like 1Password Device Trust, Twingate enables businesses to take a holistic approach to security by connecting identity, devices, and access into enforceable security programs.
We’d like to thank the 1Password team for their close collaboration on this, and we’re excited to continue investing in our technology partners!
Not a Twingate customer yet? If you’re interested in taking Twingate for a spin, you can request a personalized demo from our team or try it out yourself for free.
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Announcing Twingate's Partnership with 1Password Device Trust
Emily Lehman
•
Oct 24, 2024

Twingate’s central mission is to ensure that people can work securely from anywhere. We believe that modern security challenges are best solved by adopting a Zero Trust framework, but it’s a deceptively complex framework to operationalize.
There is a reason why the concept of Zero Trust has existed for decades, but remains relatively low in terms of full adoption: simply put, it’s really hard to do. Legacy solutions, even those in the cloud, are not built for organizations with globally distributed employees and environments spanning on-prem, cloud, and SaaS applications.
Twingate is built from the ground up to help organizations take Zero Trust concepts, and put them into practice. It all comes down to a question: Should this user, on this device, in this context, access this resource?
The ability to answer that question requires comprehensive visibility into identity, devices, and access across your entire network, which is why we’re thrilled to announce our newest partnership with 1Password Device Trust. 1Password, a leader in identity security, has expanded its offerings to fill critical gaps in access management and identity by enabling businesses to secure every sign-in to every application from every device. With this new integration, you can now verify devices in Twingate using 1Password Device Trust.
Architecture Matters
One of the main reasons Zero Trust has been so burdensome to adopt is that legacy solutions come with significant gaps.
Many organizations have already moved away from VPNs due to security, administrative, and performance downsides. Cloud proxy models were introduced over 15 years ago as the first attempt to solve these, and while they solve many of the security challenges of VPNs, they introduce their own issues around performance, reliability, and administration. All of these are compounded by the complex access questions introduced by cloud adoption and the move to distributed and hybrid workforces.
This increase in distributed workforces - especially hybrid and contractor workforces - has highlighted gaps not just in network access, but also device and identity. While historically admins focused primarily on securing company-managed devices, BYOD and third-party users who use non-company devices to access internal environments pose significant risk to security and IT teams.
The new Twingate and 1Password partnership solves these challenges by closing the gaps in security and performance on the network, identity, and device layers.
Twingate’s Enterprise Peer-to-Peer architecture establishes direct connections between devices and resources so users always get a fast, low-latency connection to work resources without compromising on security. With a dual-verification process - at the device and behind the firewall - Twingate ensures that any network connection is meticulously controlled and verified. All traffic is encrypted, and your private resources remain entirely hidden from the open internet.
To strengthen that verification process further, Twingate invests heavily in first-class integrations with leading products in modern security stacks. As a central access control layer, Twingate makes it easy to bridge together the various component solutions that form your unique security stack, including major IdPs, MDMs, EDRs, SIEMs, and more to implement an access control framework based on Zero Trust..
Partners like 1Password makes it easy for admins to apply the multiple layers of security needed to implement Defense in Depth, making it harder for malicious actors to access sensitive resources.
How it works
Within 1Password, you have the ability to granularly select requirements from an extensive library of device checks. Especially important is the ability to extend these checks to every device – even for bring-your-own devices and contractors, in addition to corporate devices managed via MDM.
Both Twingate and 1Password believe that security controls that are hard to use don’t get used at all. Because of that, we designed this integration to be simple and straightforward to implement.
Select 1Password as a verification method for Trusted Devices under the Device Security tab of the Twingate Admin Console.
Create or edit a Trusted Profile for Windows, macOS, or Linux with 1Password enabled as a verification requirement
Apply this Trusted Profile on any Twingate protected resource where 1Password device verification is required

That’s it!
Bridging Security and Usability
In today’s world, end user experience is not just a “nice to have” that can be sacrificed in the name of security.
What modern organizations are increasingly realizing is that usability is actually an important consideration for stronger security. Any tool that introduces too much friction for end users can drive a number of negative outcomes.
Both Twingate and 1Password believe security and usability shouldn’t be in conflict. In fact, they should be working together: a better end user experience leads to stronger buy-in for security programs. That means delivering both powerful security controls and a seamless end user experience.
Twingate does this by using the modern network protocol QUIC and advanced networking techniques like NAT traversal to establish direct peer-to-peer connections between users and resources. This, in combination with Twingate’s flexible deployment model, allows security teams to implement security controls for even the most niche environments and workflows without slowing down the pace of development.
1Password focuses on securing the way people already intuitively work so that the easiest path for them to take is also the most secure. Because Device Trust works equally well on business and personal devices, employees are encouraged to secure their personal devices with Device Trust because that is the easiest way to access applications.
Building the Zero Trust ecosystem
At Twingate integrations aren’t just another “nice to have” feature. Despite how the market often portrays it, Zero Trust is a framework, not a single solution. That means any organization will need multiple tools in order to actually see the security benefits of a Zero Trust model in action.
And yet very few of those tools actually play nicely. We believe it’s critical to build a product that doesn’t just work with, but actually enhances the benefits of other cybersecurity tools.
Partnering with solutions like 1Password Device Trust, Twingate enables businesses to take a holistic approach to security by connecting identity, devices, and access into enforceable security programs.
We’d like to thank the 1Password team for their close collaboration on this, and we’re excited to continue investing in our technology partners!
Not a Twingate customer yet? If you’re interested in taking Twingate for a spin, you can request a personalized demo from our team or try it out yourself for free.
Solutions
Solutions
The VPN replacement your workforce will love.
Solutions