Simple & Secure Access to GitLab on AWS
Jimmy Li
•
Mar 4, 2022

If you use AWS, what’s the best way to securely access your AWS resources like GitLab? One option is to use a VPN like AWS Client VPN, but the setup process can be quite involved and there are hidden costs. An alternative is a Zero Trust solution like Twingate.
In this guide, we’ll walk through how in just a few minutes, you can set up secure access to GitLab and all of your other AWS resources with just a single line of code using Twingate. If you run things on GCP or on-prem as well, you can also use Twingate as a single solution to manage your hybrid or multi-cloud architecture.
🎥 Video tutorial: How to securely access GitLab and other AWS resources using Twingate in 4 minutes
Please also join us in our community forum to share and discuss your experience and any other use cases you’ve discovered!
Prerequisites
If you haven’t already, launch an EC2 instance. This will be where we’ll deploy the Twingate Connector later on. We support all major Linux distributions.
The Twingate Connector will grant you access to your cloud resources. If you haven’t done so already, the video below shows how to deploy an example resource on AWS. Note that you don’t need Public IP addresses for these resources — Twingate will be able to connect to them via just their Private IP addresses.
Video tutorial: How to deploy a resource on AWS
Sign up for Twingate
Twingate Starter is a new free plan that is designed for personal use and small teams. If you don’t have an account already, please click here and follow the simple steps to sign up for a Starter account and begin the initial setup. Once you have an account, there are 5 simple steps to get up and running.
1. Create a Remote Network
After creating a Twingate account, from the main “Network‚ page, add a new Remote Network and give it a name. This represents the network we’re going to connect to — in this case, that would be AWS.
Video tutorial: How to create a Remote Network
2. Add a Connector
The next step is to deploy a Twingate Connector, which is a piece of software that allows for secure access to your remote network and the services running on it. In addition to AWS, it can also be deployed to other cloud instances (GCP, Azure, etc.) as well as your home devices, including Synology NAS and Raspberry Pi.
Generate Connector tokens
In this case, we’ll set it up on AWS. Click on one of the automatically generated Connectors (the names are random) and complete the following steps:
Click on Linux as the deployment method
Generate tokens. You’ll be prompted to sign in again, after which you should see two new tokens.
Copy the automatically generated shell command. You will soon run this command on your EC2 instance to install the Connector there.
Video tutorial: How to generate Connector tokens
Deploy the Connector on the Remote Network
If you don’t already have one, create a new VM instance on AWS where we’ll deploy the Twingate Connector. We suggest giving the VM instance the same name as the Connector for easy association. After the instance is up and running, connect to it using whichever method you prefer and paste in the command that was automatically generated by your Twingate Connector. After the command completes, you should see that the Connector status has turned green, indicating that it was successfully deployed.
Video tutorial: How to deploy a Connector on AWS
3. Add a Resource
Now that you’ve deployed a Twingate Connector on AWS, you can get remote access to any other resource running on the same VPC subnet. You can configure your resources not to have a Public IP address, but you will still be able to access them via Twingate.
Go back to your Remote Network and click on the “Add Resource‚ link. In the popup, click on the “CIDR Address‚ box, choose a Label name for the Resource, enter the private IP address of your resource’s VM instance, and click “Add Resource‚. Congrats! You now have secure, private access to GitLab on AWS. The same steps can be repeated for any other AWS resources you have.
Video tutorial: How to add a Resource
4. Download the Twingate client
All that’s left to do now is to install Twingate on your device (we support Windows, Mac, Linux and have apps for iOS and Android) to authenticate your account and authorize your access to the instance. As an example, let’s walk through setting up the Twingate client on macOS.
First, download and install the macOS app here. Type in the Network URL that you chose when you signed up (the [abc] part of [abc].twingate.com) and click “Join Network‚. You’ll be asked to log in using the same account you used to sign up. After signing in, you’ll see that Twingate is connected with access to the Resource you created. Click on “Open in Browser…‚ and you should see your resource is accessible via the Private IP address of your VM instance, even though it has no public IP address.
Finally, disconnect from Twingate and try accessing the resource again — you should see that it’s completely inaccessible.
Video tutorial: How to access your Resource using the Twingate client
Congrats! You’ve finished setting up Twingate for AWS and used it to get secure access to GitLab. Anything else that you deploy to the same VPC (e.g., a web app, dashboard, database, etc.) can also be added as a Resource, and you would have secure access for those as well using the same Connector.
If you also run things on GCP or on-prem, you can use Twingate as a single solution to manage your hybrid or multi-cloud architecture. Just follow similar steps to deploy connectors on each network, or use our API to configure everything programmatically. And as the end user, Twingate’s client app is all you need to get secure access to all of your resources.
Join us in the community forum to share how things went and what cool use cases you’ve discovered!
5. Sharing is Caring
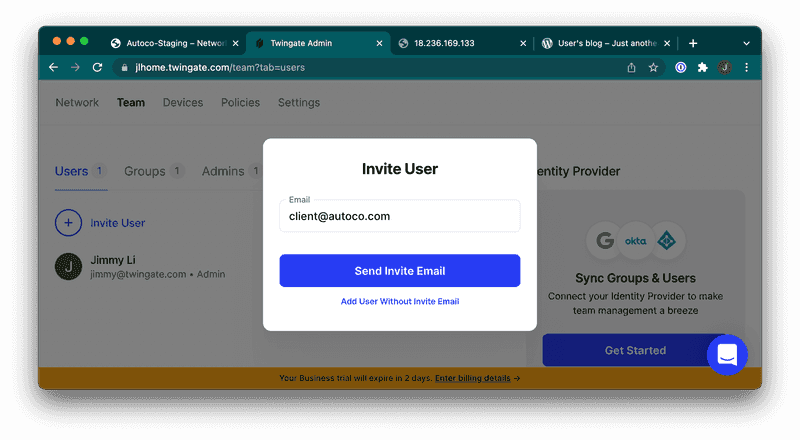
Do you want to share access to the resource with a teammate, client, or friend? You can easily do this from the Twingate web UI. Just go to the “Team‚ tab and click “Invite User‚ to send an email invitation. The recipient would simply follow the same steps to download the Twingate client, join your network, and get access to any resource you want!
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Simple & Secure Access to GitLab on AWS
Jimmy Li
•
Mar 4, 2022

If you use AWS, what’s the best way to securely access your AWS resources like GitLab? One option is to use a VPN like AWS Client VPN, but the setup process can be quite involved and there are hidden costs. An alternative is a Zero Trust solution like Twingate.
In this guide, we’ll walk through how in just a few minutes, you can set up secure access to GitLab and all of your other AWS resources with just a single line of code using Twingate. If you run things on GCP or on-prem as well, you can also use Twingate as a single solution to manage your hybrid or multi-cloud architecture.
🎥 Video tutorial: How to securely access GitLab and other AWS resources using Twingate in 4 minutes
Please also join us in our community forum to share and discuss your experience and any other use cases you’ve discovered!
Prerequisites
If you haven’t already, launch an EC2 instance. This will be where we’ll deploy the Twingate Connector later on. We support all major Linux distributions.
The Twingate Connector will grant you access to your cloud resources. If you haven’t done so already, the video below shows how to deploy an example resource on AWS. Note that you don’t need Public IP addresses for these resources — Twingate will be able to connect to them via just their Private IP addresses.
Video tutorial: How to deploy a resource on AWS
Sign up for Twingate
Twingate Starter is a new free plan that is designed for personal use and small teams. If you don’t have an account already, please click here and follow the simple steps to sign up for a Starter account and begin the initial setup. Once you have an account, there are 5 simple steps to get up and running.
1. Create a Remote Network
After creating a Twingate account, from the main “Network‚ page, add a new Remote Network and give it a name. This represents the network we’re going to connect to — in this case, that would be AWS.
Video tutorial: How to create a Remote Network
2. Add a Connector
The next step is to deploy a Twingate Connector, which is a piece of software that allows for secure access to your remote network and the services running on it. In addition to AWS, it can also be deployed to other cloud instances (GCP, Azure, etc.) as well as your home devices, including Synology NAS and Raspberry Pi.
Generate Connector tokens
In this case, we’ll set it up on AWS. Click on one of the automatically generated Connectors (the names are random) and complete the following steps:
Click on Linux as the deployment method
Generate tokens. You’ll be prompted to sign in again, after which you should see two new tokens.
Copy the automatically generated shell command. You will soon run this command on your EC2 instance to install the Connector there.
Video tutorial: How to generate Connector tokens
Deploy the Connector on the Remote Network
If you don’t already have one, create a new VM instance on AWS where we’ll deploy the Twingate Connector. We suggest giving the VM instance the same name as the Connector for easy association. After the instance is up and running, connect to it using whichever method you prefer and paste in the command that was automatically generated by your Twingate Connector. After the command completes, you should see that the Connector status has turned green, indicating that it was successfully deployed.
Video tutorial: How to deploy a Connector on AWS
3. Add a Resource
Now that you’ve deployed a Twingate Connector on AWS, you can get remote access to any other resource running on the same VPC subnet. You can configure your resources not to have a Public IP address, but you will still be able to access them via Twingate.
Go back to your Remote Network and click on the “Add Resource‚ link. In the popup, click on the “CIDR Address‚ box, choose a Label name for the Resource, enter the private IP address of your resource’s VM instance, and click “Add Resource‚. Congrats! You now have secure, private access to GitLab on AWS. The same steps can be repeated for any other AWS resources you have.
Video tutorial: How to add a Resource
4. Download the Twingate client
All that’s left to do now is to install Twingate on your device (we support Windows, Mac, Linux and have apps for iOS and Android) to authenticate your account and authorize your access to the instance. As an example, let’s walk through setting up the Twingate client on macOS.
First, download and install the macOS app here. Type in the Network URL that you chose when you signed up (the [abc] part of [abc].twingate.com) and click “Join Network‚. You’ll be asked to log in using the same account you used to sign up. After signing in, you’ll see that Twingate is connected with access to the Resource you created. Click on “Open in Browser…‚ and you should see your resource is accessible via the Private IP address of your VM instance, even though it has no public IP address.
Finally, disconnect from Twingate and try accessing the resource again — you should see that it’s completely inaccessible.
Video tutorial: How to access your Resource using the Twingate client
Congrats! You’ve finished setting up Twingate for AWS and used it to get secure access to GitLab. Anything else that you deploy to the same VPC (e.g., a web app, dashboard, database, etc.) can also be added as a Resource, and you would have secure access for those as well using the same Connector.
If you also run things on GCP or on-prem, you can use Twingate as a single solution to manage your hybrid or multi-cloud architecture. Just follow similar steps to deploy connectors on each network, or use our API to configure everything programmatically. And as the end user, Twingate’s client app is all you need to get secure access to all of your resources.
Join us in the community forum to share how things went and what cool use cases you’ve discovered!
5. Sharing is Caring
Do you want to share access to the resource with a teammate, client, or friend? You can easily do this from the Twingate web UI. Just go to the “Team‚ tab and click “Invite User‚ to send an email invitation. The recipient would simply follow the same steps to download the Twingate client, join your network, and get access to any resource you want!

Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Simple & Secure Access to GitLab on AWS
Jimmy Li
•
Mar 4, 2022

If you use AWS, what’s the best way to securely access your AWS resources like GitLab? One option is to use a VPN like AWS Client VPN, but the setup process can be quite involved and there are hidden costs. An alternative is a Zero Trust solution like Twingate.
In this guide, we’ll walk through how in just a few minutes, you can set up secure access to GitLab and all of your other AWS resources with just a single line of code using Twingate. If you run things on GCP or on-prem as well, you can also use Twingate as a single solution to manage your hybrid or multi-cloud architecture.
🎥 Video tutorial: How to securely access GitLab and other AWS resources using Twingate in 4 minutes
Please also join us in our community forum to share and discuss your experience and any other use cases you’ve discovered!
Prerequisites
If you haven’t already, launch an EC2 instance. This will be where we’ll deploy the Twingate Connector later on. We support all major Linux distributions.
The Twingate Connector will grant you access to your cloud resources. If you haven’t done so already, the video below shows how to deploy an example resource on AWS. Note that you don’t need Public IP addresses for these resources — Twingate will be able to connect to them via just their Private IP addresses.
Video tutorial: How to deploy a resource on AWS
Sign up for Twingate
Twingate Starter is a new free plan that is designed for personal use and small teams. If you don’t have an account already, please click here and follow the simple steps to sign up for a Starter account and begin the initial setup. Once you have an account, there are 5 simple steps to get up and running.
1. Create a Remote Network
After creating a Twingate account, from the main “Network‚ page, add a new Remote Network and give it a name. This represents the network we’re going to connect to — in this case, that would be AWS.
Video tutorial: How to create a Remote Network
2. Add a Connector
The next step is to deploy a Twingate Connector, which is a piece of software that allows for secure access to your remote network and the services running on it. In addition to AWS, it can also be deployed to other cloud instances (GCP, Azure, etc.) as well as your home devices, including Synology NAS and Raspberry Pi.
Generate Connector tokens
In this case, we’ll set it up on AWS. Click on one of the automatically generated Connectors (the names are random) and complete the following steps:
Click on Linux as the deployment method
Generate tokens. You’ll be prompted to sign in again, after which you should see two new tokens.
Copy the automatically generated shell command. You will soon run this command on your EC2 instance to install the Connector there.
Video tutorial: How to generate Connector tokens
Deploy the Connector on the Remote Network
If you don’t already have one, create a new VM instance on AWS where we’ll deploy the Twingate Connector. We suggest giving the VM instance the same name as the Connector for easy association. After the instance is up and running, connect to it using whichever method you prefer and paste in the command that was automatically generated by your Twingate Connector. After the command completes, you should see that the Connector status has turned green, indicating that it was successfully deployed.
Video tutorial: How to deploy a Connector on AWS
3. Add a Resource
Now that you’ve deployed a Twingate Connector on AWS, you can get remote access to any other resource running on the same VPC subnet. You can configure your resources not to have a Public IP address, but you will still be able to access them via Twingate.
Go back to your Remote Network and click on the “Add Resource‚ link. In the popup, click on the “CIDR Address‚ box, choose a Label name for the Resource, enter the private IP address of your resource’s VM instance, and click “Add Resource‚. Congrats! You now have secure, private access to GitLab on AWS. The same steps can be repeated for any other AWS resources you have.
Video tutorial: How to add a Resource
4. Download the Twingate client
All that’s left to do now is to install Twingate on your device (we support Windows, Mac, Linux and have apps for iOS and Android) to authenticate your account and authorize your access to the instance. As an example, let’s walk through setting up the Twingate client on macOS.
First, download and install the macOS app here. Type in the Network URL that you chose when you signed up (the [abc] part of [abc].twingate.com) and click “Join Network‚. You’ll be asked to log in using the same account you used to sign up. After signing in, you’ll see that Twingate is connected with access to the Resource you created. Click on “Open in Browser…‚ and you should see your resource is accessible via the Private IP address of your VM instance, even though it has no public IP address.
Finally, disconnect from Twingate and try accessing the resource again — you should see that it’s completely inaccessible.
Video tutorial: How to access your Resource using the Twingate client
Congrats! You’ve finished setting up Twingate for AWS and used it to get secure access to GitLab. Anything else that you deploy to the same VPC (e.g., a web app, dashboard, database, etc.) can also be added as a Resource, and you would have secure access for those as well using the same Connector.
If you also run things on GCP or on-prem, you can use Twingate as a single solution to manage your hybrid or multi-cloud architecture. Just follow similar steps to deploy connectors on each network, or use our API to configure everything programmatically. And as the end user, Twingate’s client app is all you need to get secure access to all of your resources.
Join us in the community forum to share how things went and what cool use cases you’ve discovered!
5. Sharing is Caring
Do you want to share access to the resource with a teammate, client, or friend? You can easily do this from the Twingate web UI. Just go to the “Team‚ tab and click “Invite User‚ to send an email invitation. The recipient would simply follow the same steps to download the Twingate client, join your network, and get access to any resource you want!

Solutions
Solutions
The VPN replacement your workforce will love.
Solutions