The Best 10 Alternatives to UH VPN (+ Pricing & Reviews)
Twingate Team
•
•
Jul 27, 2024
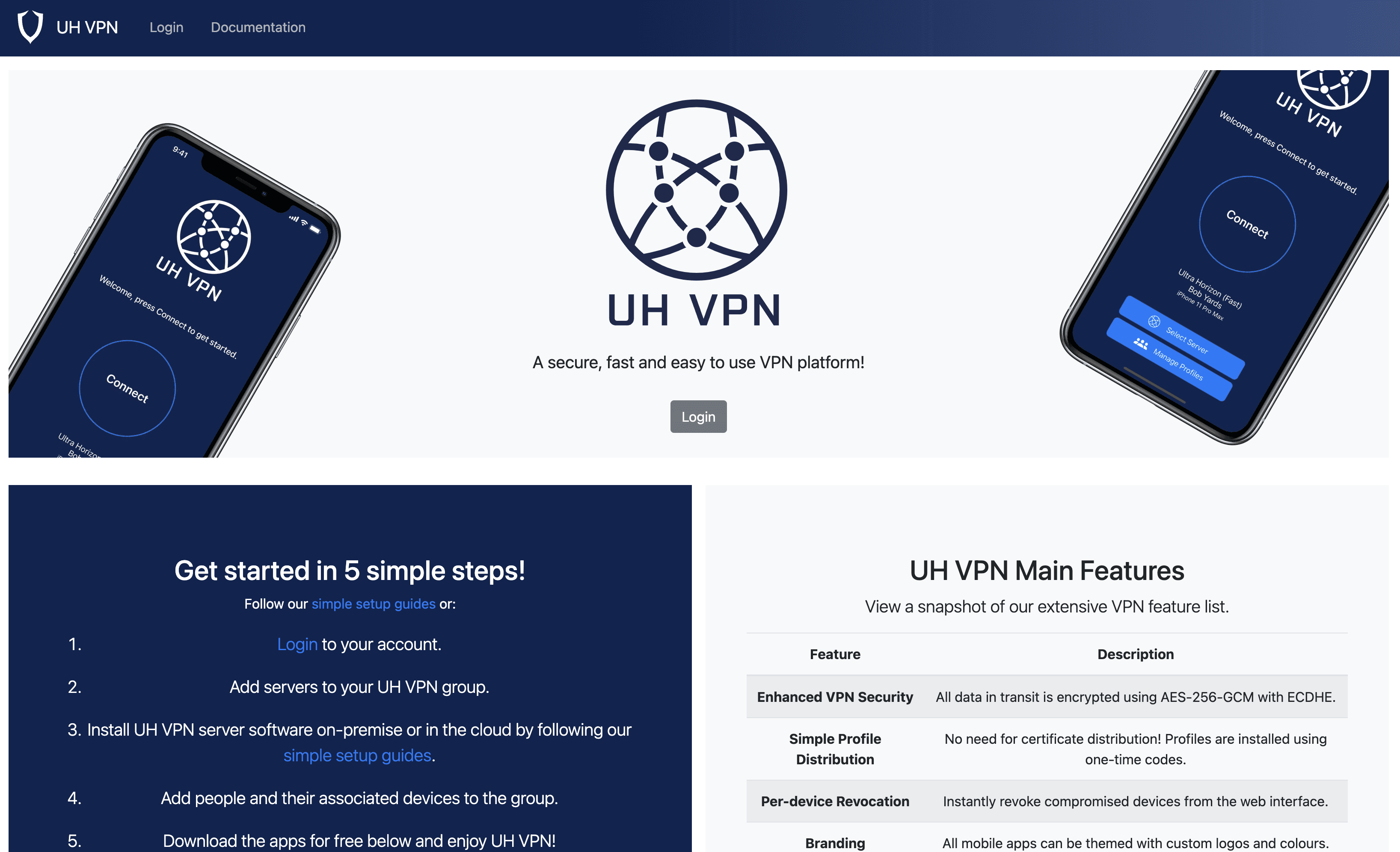
UH VPN is a secure, fast, and easy-to-use VPN platform designed to enhance online privacy and security. It offers features like enhanced security, simple profile distribution, and per-device revocation. However, UH VPN might not be the choice for everyone. This article explores the benefits and limitations of UH VPN.
10 Alternatives to UH VPN
1. Twingate
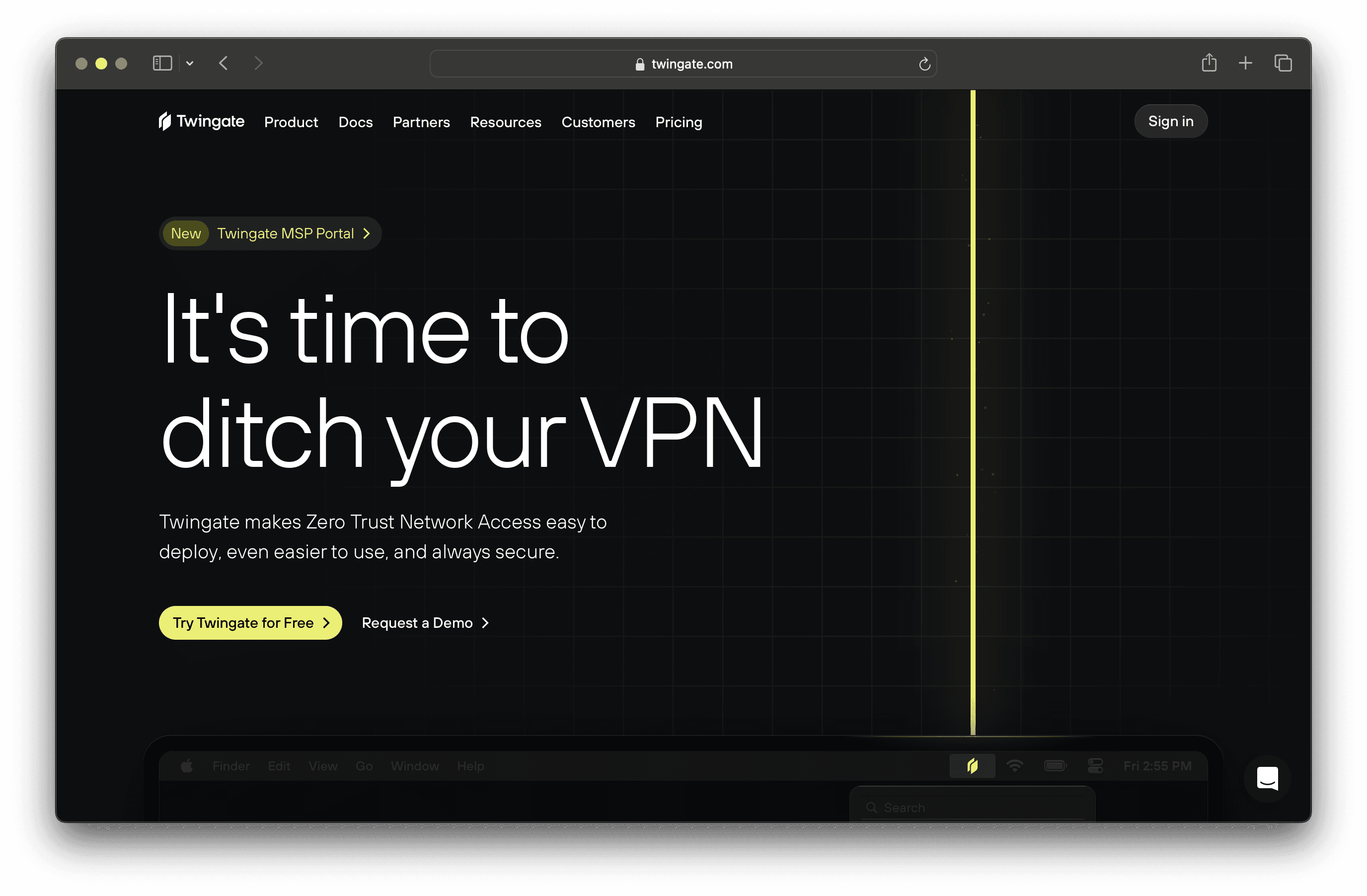
Twingate is a network security solution designed to replace traditional VPNs for remote access, offering a zero-trust security model and seamless deployment alongside existing infrastructure. With a focus on ease of use and scalability, Twingate aims to provide a secure and maintainable solution for businesses of all sizes.
Twingate Pricing
Starter: Free per user/month
Teams: $6 per user/month (monthly), $5 per user/month (yearly)
Business: $12 per user/month (monthly), $10 per user/month (yearly)
Enterprise: Custom pricing per user/month
Twingate Reviews
Twingate has an overall rating of 4.7 out of 5 stars based on 63 reviews. Users praise its ease of setup and high security. Check out more of our reviews here!
Pros and Cons of Twingate
Pros:
Enhanced Security: Twingate's zero trust model ensures that only authenticated users can access specific resources, significantly reducing the risk of unauthorized access.
Ease of Deployment: Setting up Twingate is straightforward and quick, allowing businesses to implement it without extensive technical expertise or prolonged downtime.
High Performance: Users consistently report that Twingate offers faster and more reliable connections compared to traditional VPN solutions, enhancing overall productivity.
Cons:
Initial Learning Curve: Some users may find the initial setup and understanding of zero trust principles challenging, especially if they are new to this security model.
Internet Dependency: As a cloud-based solution, Twingate's performance is reliant on stable internet connectivity, which can be a limitation in areas with poor internet service.
Limited Customization: While Twingate offers robust features, some users have noted that the platform lacks certain customization options that might be necessary for specific use cases.
2. Zscaler
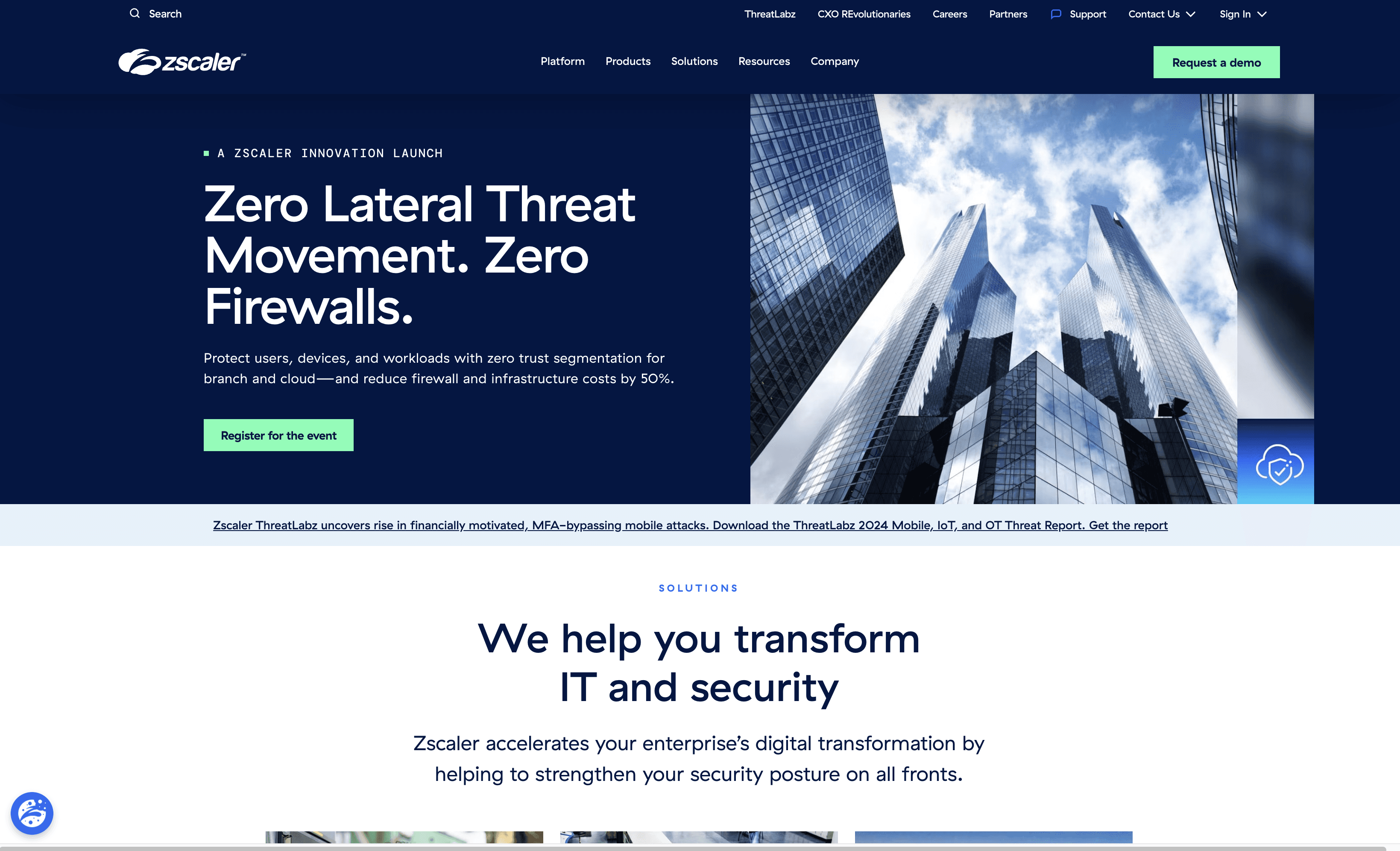
Zscaler is a cybersecurity solution that replaces traditional VPNs with a zero-trust model, ensuring secure access to applications and data. It offers seamless deployment and scalability, making it ideal for businesses of all sizes. Zscaler focuses on securing users, cloud workloads, and IoT/OT devices.
Zscaler Pricing
Zscaler's pricing is not public. Contact their support for more info.
Zscaler Reviews
Zscaler has an overall rating of 4.5 out of 5 stars based on 43 reviews. Users praise its robust security and ease of use. Check out more of our reviews here!
Pros and Cons ofZscaler
Pros:
Comprehensive Security: Zscaler offers extensive security solutions, including cyberthreat protection and data protection, ensuring robust defense mechanisms.
Zero Trust Architecture: Provides zero trust connectivity for users, workloads, IoT/OT devices, and B2B applications, enhancing overall security.
Recognition and Trust: Recognized as a leader in the Gartner Magic Quadrant for Security Service Edge (SSE), trusted by 35% of Global 2000 companies.
Cons:
Complexity for New Users: The extensive range of products and solutions might be overwhelming for new users or smaller organizations.
Dependency on Cloud: Heavy reliance on cloud infrastructure, which may not be suitable for all organizations, especially those with strict data residency requirements.
Cost Considerations: Potentially high costs associated with comprehensive security solutions and zero trust architecture, which might be a barrier for smaller enterprises.
3. Azure VPN Gateway
Azure VPN Gateway is a service that allows users to securely connect to the cloud. It offers seamless integration with existing infrastructure and supports various account options, including free and pay-as-you-go plans. Designed for scalability and ease of use, it aims to provide secure and reliable cloud connectivity for businesses.
Azure VPN Gateway Pricing
Azure Free Account: $200 credit for 30 days
Pay as You Go: Pay only for what you use
Azure VPN Gateway Reviews
Azure VPN Gateway has an overall rating of 4.1 out of 5 stars based on 21 reviews. Users appreciate its reliability and security. Check out more of our reviews here!
Pros and Cons of Azure VPN Gateway
Pros:
Secure Connection: Ensures secure connections to the cloud using industry-standard protocols like IPsec and IKE.
Ease of Setup: Many users find Azure VPN Gateway easy to set up and configure, reducing deployment time.
Reliability: Users appreciate the reliability and minimal downtime, ensuring consistent access to resources.
Cons:
Certificate Generation: The process of generating certificates can be cumbersome and is considered outdated by some users.
Cost: While there are free options, extensive use beyond the free tier can incur significant costs.
Implementation Time: It can take time to implement, which might be a drawback for some users.
4. CyberGhost
CyberGhost VPN is a service designed to ensure online privacy and security. It offers strong encryption, a no-logs policy, and fast speeds across a large server fleet. With support for multiple devices and 24/7 customer service, CyberGhost aims to provide a reliable and user-friendly VPN experience.
CyberGhost Pricing
1 Month Plan: $12.99 per month
28 Month Plan: $2.03 per month, billed $56.94 for the first 2 years and yearly thereafter
6 Month Plan: $6.99 per month, billed $41.94 every 6 months
CyberGhost Reviews
CyberGhost has an overall rating of 4.5 out of 5 stars based on 20 reviews. Users praise its wide array of server locations. Check out more of our reviews here!
Pros and Cons of CyberGhost
Pros:
Complete Privacy: CyberGhost's no-logs policy and strong encryption ensure your online activities remain private and secure.
Device Compatibility: Supports up to 7 devices simultaneously, making it ideal for families or small teams.
Large Server Fleet: Access to servers in 100 countries, providing extensive global coverage and flexibility.
Cons:
Access Issues: Some users report occasional difficulties accessing certain websites or services.
Limited Location Options: Despite a large server fleet, some regions may have fewer server options.
Connectivity Issues: Users have experienced intermittent connectivity problems, affecting the reliability of the service.
5. Watchguard
WatchGuard provides comprehensive cybersecurity solutions designed to protect businesses of all sizes. With features like AI-driven network detection, unified security platforms, and 24/7 managed detection and response, WatchGuard aims to deliver robust, scalable, and user-friendly security solutions for modern enterprises.
Watchguard Pricing
Watchguard's pricing is not public. Contact their support for more info.
Watchguard Reviews
WatchGuard has an overall rating of 4.7 out of 5 stars based on 258 reviews. Users appreciate its ease of use and strong security features. Check out more of our reviews here!
Pros and Cons of Watchguard
Pros:
Comprehensive Security: WatchGuard offers a unified approach, simplifying the deployment and management of various security products and services.
Clarity & Control: The WatchGuard Cloud provides centralized security administration, enhanced visibility, and advanced reporting capabilities.
Shared Knowledge: Integrated knowledge-sharing capabilities enable a true XDR-based security strategy and a zero trust, identity-based security posture.
Cons:
Complexity for Small Businesses: Advanced features may overwhelm small businesses with limited IT resources.
Cost: Enterprise-grade, AI-enabled network detection and response capabilities can be costly for smaller organizations.
Dependency on Cloud: Heavy reliance on cloud-based management may not suit organizations with strict data residency requirements.
6. Palo Alto Networks

Palo Alto Networks offers advanced cybersecurity solutions designed to protect businesses from modern threats. Utilizing AI-driven technology, their platform provides comprehensive security across networks, clouds, and endpoints. With a focus on simplicity and efficiency, Palo Alto Networks aims to deliver robust protection while streamlining security operations for organizations of all sizes.
Palo Alto Networks Pricing
Palo Alto Networks' pricing is not public. Contact their support for more info.
Palo Alto Networks Reviews
Palo Alto Networks has an overall rating of 4.4 out of 5 stars based on 208 reviews. Users appreciate its robust security and ease of use. Check out more of our reviews here!
Pros and Cons of Palo Alto Networks
Pros:
AI-Powered Security: Precision AI enhances threat detection and remediation, providing proactive protection against sophisticated cyber threats.
Comprehensive Solutions: Offers extensive security solutions for network, cloud, and security operations, ensuring robust defense mechanisms.
Industry Recognition: Recognized as a leader in multiple Gartner Magic Quadrants and Forrester Waves, showcasing its credibility and reliability.
Cons:
Complexity: The wide range of products and services can be overwhelming for users, requiring significant time to navigate and implement effectively.
Cost: High-end security solutions and services can be expensive, potentially limiting accessibility for smaller organizations with tight budgets.
Learning Curve: Advanced features and AI-driven solutions may require significant training and expertise, posing a challenge for new users.
7. ClearVPN
ClearVPN is a user-friendly VPN service designed to enhance online privacy and security. With a focus on simplicity and powerful technology, ClearVPN offers seamless connectivity and optimal performance for various online activities, ensuring a hassle-free experience for users of all technical levels.
ClearVPN Pricing
1 Month Plan: $9.99 per month
1 Year Plan: $3.75 per month, billed annually at $44.99
ClearVPN Reviews
ClearVPN has an overall rating of 4.3 out of 5 stars based on 10 reviews. Users appreciate its ease of use and fast speeds. Check out more of our reviews here!
Pros and Cons of ClearVPN
Pros:
Ease of Use: ClearVPN's one-tap interface simplifies the process, making it accessible for all users.
Enhanced Security: High-level encryption and advanced VPN protocols ensure robust user privacy and security.
Fast Servers: Optimized servers in over 45 countries provide excellent speed and performance.
Cons:
Limited Compatibility: The Mac version does not support older operating systems, limiting its usability.
Interface Inconsistencies: Different interfaces across devices may confuse users switching between them.
Subscription Requirement: Full features and benefits are locked behind a premium subscription.
8. Todyl
Todyl is a cybersecurity platform offering a modular and comprehensive approach to security. Designed for ease of use and scalability, Todyl consolidates multiple security capabilities into a single-agent platform, making it ideal for businesses of all sizes. It ensures robust protection while simplifying deployment and management.
Todyl Pricing
Todyl's pricing is not public. Contact their support for more info.
Todyl Reviews
Todyl has an overall rating of 4.7 out of 5 stars based on 41 reviews. Users appreciate its ease of use and customer support. Check out more of our reviews here!
Pros and Cons of Todyl
Pros:
Comprehensive Security: Todyl offers a consolidated, customizable cybersecurity platform, ensuring robust protection across various modules.
Ease of Use: Simplifies management and deployment, making it accessible for IT teams to own and operate cybersecurity effectively.
Customer Support: Highly praised by users for responsive and helpful support, enhancing overall user experience.
Cons:
Technical Issues: Some users report occasional technical problems, affecting the platform's reliability.
Integration Issues: Challenges with integrating Todyl with existing systems have been noted by several users.
Pricing Concerns: The cost of Todyl's comprehensive solutions can be a barrier for smaller organizations.
9. SaferVPN

SaferVPN is a user-friendly VPN service designed to enhance online privacy and security. It offers fast speeds, strong encryption, and a no-logs policy, ensuring a secure and private browsing experience. With support for multiple devices, SaferVPN aims to provide reliable and accessible protection for all users.
SaferVPN Pricing
1 Month Plan: $12.95 per month
1 Year Plan: $5.49 per month, billed annually at $65.88
3 Year Plan: $2.50 per month, billed $89.99 every 3 years
SaferVPN Reviews
SaferVPN has an overall rating of 4.3 out of 5 stars based on 60 reviews. Users appreciate its ease of use and strong security features. Check out more of our reviews here!
Pros and Cons of SaferVPN
Pros:
Ease of Use: SaferVPN's intuitive interface makes it accessible for users of all technical levels, ensuring a smooth and hassle-free experience.
Customer Support: Responsive and helpful customer support enhances user satisfaction, providing timely assistance and resolving issues efficiently.
Privacy Protection: Strong encryption and a strict no-logs policy ensure that user data remains private and secure, safeguarding online activities.
Cons:
Slow Speed: Some users report slower connection speeds, which can affect streaming and downloading activities.
Expensive: The cost of SaferVPN's plans may be a barrier for budget-conscious users, especially when compared to competitors.
Limited Location Options: Despite a decent server variety, some regions have fewer server options, limiting flexibility for users in those areas.
10. Proton VPN
Proton VPN is a secure, fast VPN service designed to protect user privacy and provide unrestricted internet access. Based in Switzerland, it ensures strong privacy protections and a strict no-logs policy. Proton VPN offers seamless connectivity and optimal performance for various online activities, making it user-friendly and reliable.
Proton VPN Pricing
1-month plan: $9.99/month
1-year plan: $4.99/month (billed $59.88 annually)
2-year plan: $4.49/month (billed $107.76 biennially)
Proton Free: Free forever
Proton VPN Reviews
Proton VPN has an overall rating of 4.0 out of 5 stars based on 2 reviews. Users appreciate its robust security features and strong encryption. Check out more of our reviews here!
Pros and Cons of Proton VPN
Pros:
Swiss-based: Proton VPN is headquartered in Switzerland, ensuring strong privacy laws and protection from EU and US jurisdiction.
Strict no-logs policy: Proton VPN does not track or record user activity, ensuring complete privacy.
Multi-platform support: Available on Windows, macOS, Linux, Chromebook, Android, Android TV, and iOS/iPadOS, offering flexibility.
Cons:
Speed on Free Plan: The free version may not offer the same speed and features as the paid plans, affecting performance.
Limited Free Servers: The free version has limited server options compared to the paid plans, restricting choices.
Cost of Paid Plans: Users seeking faster speeds and more features need to subscribe to a paid plan, which can be costly.
Looking to secure your technical infrastructure?
Twingate offers granular access controls and deployment automations to protect your VPC environment. By leveraging Zero Trust security tools, Twingate ensures that private resources and internet traffic remain secure, making it an ideal solution for modern businesses. Try Twingate for Free today!
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
The Best 10 Alternatives to UH VPN (+ Pricing & Reviews)
Twingate Team
•
•
Jul 27, 2024

UH VPN is a secure, fast, and easy-to-use VPN platform designed to enhance online privacy and security. It offers features like enhanced security, simple profile distribution, and per-device revocation. However, UH VPN might not be the choice for everyone. This article explores the benefits and limitations of UH VPN.

10 Alternatives to UH VPN
1. Twingate

Twingate is a network security solution designed to replace traditional VPNs for remote access, offering a zero-trust security model and seamless deployment alongside existing infrastructure. With a focus on ease of use and scalability, Twingate aims to provide a secure and maintainable solution for businesses of all sizes.
Twingate Pricing
Starter: Free per user/month
Teams: $6 per user/month (monthly), $5 per user/month (yearly)
Business: $12 per user/month (monthly), $10 per user/month (yearly)
Enterprise: Custom pricing per user/month
Twingate Reviews
Twingate has an overall rating of 4.7 out of 5 stars based on 63 reviews. Users praise its ease of setup and high security. Check out more of our reviews here!
Pros and Cons of Twingate
Pros:
Enhanced Security: Twingate's zero trust model ensures that only authenticated users can access specific resources, significantly reducing the risk of unauthorized access.
Ease of Deployment: Setting up Twingate is straightforward and quick, allowing businesses to implement it without extensive technical expertise or prolonged downtime.
High Performance: Users consistently report that Twingate offers faster and more reliable connections compared to traditional VPN solutions, enhancing overall productivity.
Cons:
Initial Learning Curve: Some users may find the initial setup and understanding of zero trust principles challenging, especially if they are new to this security model.
Internet Dependency: As a cloud-based solution, Twingate's performance is reliant on stable internet connectivity, which can be a limitation in areas with poor internet service.
Limited Customization: While Twingate offers robust features, some users have noted that the platform lacks certain customization options that might be necessary for specific use cases.
2. Zscaler

Zscaler is a cybersecurity solution that replaces traditional VPNs with a zero-trust model, ensuring secure access to applications and data. It offers seamless deployment and scalability, making it ideal for businesses of all sizes. Zscaler focuses on securing users, cloud workloads, and IoT/OT devices.
Zscaler Pricing
Zscaler's pricing is not public. Contact their support for more info.
Zscaler Reviews
Zscaler has an overall rating of 4.5 out of 5 stars based on 43 reviews. Users praise its robust security and ease of use. Check out more of our reviews here!
Pros and Cons ofZscaler
Pros:
Comprehensive Security: Zscaler offers extensive security solutions, including cyberthreat protection and data protection, ensuring robust defense mechanisms.
Zero Trust Architecture: Provides zero trust connectivity for users, workloads, IoT/OT devices, and B2B applications, enhancing overall security.
Recognition and Trust: Recognized as a leader in the Gartner Magic Quadrant for Security Service Edge (SSE), trusted by 35% of Global 2000 companies.
Cons:
Complexity for New Users: The extensive range of products and solutions might be overwhelming for new users or smaller organizations.
Dependency on Cloud: Heavy reliance on cloud infrastructure, which may not be suitable for all organizations, especially those with strict data residency requirements.
Cost Considerations: Potentially high costs associated with comprehensive security solutions and zero trust architecture, which might be a barrier for smaller enterprises.
3. Azure VPN Gateway

Azure VPN Gateway is a service that allows users to securely connect to the cloud. It offers seamless integration with existing infrastructure and supports various account options, including free and pay-as-you-go plans. Designed for scalability and ease of use, it aims to provide secure and reliable cloud connectivity for businesses.
Azure VPN Gateway Pricing
Azure Free Account: $200 credit for 30 days
Pay as You Go: Pay only for what you use
Azure VPN Gateway Reviews
Azure VPN Gateway has an overall rating of 4.1 out of 5 stars based on 21 reviews. Users appreciate its reliability and security. Check out more of our reviews here!
Pros and Cons of Azure VPN Gateway
Pros:
Secure Connection: Ensures secure connections to the cloud using industry-standard protocols like IPsec and IKE.
Ease of Setup: Many users find Azure VPN Gateway easy to set up and configure, reducing deployment time.
Reliability: Users appreciate the reliability and minimal downtime, ensuring consistent access to resources.
Cons:
Certificate Generation: The process of generating certificates can be cumbersome and is considered outdated by some users.
Cost: While there are free options, extensive use beyond the free tier can incur significant costs.
Implementation Time: It can take time to implement, which might be a drawback for some users.
4. CyberGhost

CyberGhost VPN is a service designed to ensure online privacy and security. It offers strong encryption, a no-logs policy, and fast speeds across a large server fleet. With support for multiple devices and 24/7 customer service, CyberGhost aims to provide a reliable and user-friendly VPN experience.
CyberGhost Pricing
1 Month Plan: $12.99 per month
28 Month Plan: $2.03 per month, billed $56.94 for the first 2 years and yearly thereafter
6 Month Plan: $6.99 per month, billed $41.94 every 6 months
CyberGhost Reviews
CyberGhost has an overall rating of 4.5 out of 5 stars based on 20 reviews. Users praise its wide array of server locations. Check out more of our reviews here!
Pros and Cons of CyberGhost
Pros:
Complete Privacy: CyberGhost's no-logs policy and strong encryption ensure your online activities remain private and secure.
Device Compatibility: Supports up to 7 devices simultaneously, making it ideal for families or small teams.
Large Server Fleet: Access to servers in 100 countries, providing extensive global coverage and flexibility.
Cons:
Access Issues: Some users report occasional difficulties accessing certain websites or services.
Limited Location Options: Despite a large server fleet, some regions may have fewer server options.
Connectivity Issues: Users have experienced intermittent connectivity problems, affecting the reliability of the service.
5. Watchguard

WatchGuard provides comprehensive cybersecurity solutions designed to protect businesses of all sizes. With features like AI-driven network detection, unified security platforms, and 24/7 managed detection and response, WatchGuard aims to deliver robust, scalable, and user-friendly security solutions for modern enterprises.
Watchguard Pricing
Watchguard's pricing is not public. Contact their support for more info.
Watchguard Reviews
WatchGuard has an overall rating of 4.7 out of 5 stars based on 258 reviews. Users appreciate its ease of use and strong security features. Check out more of our reviews here!
Pros and Cons of Watchguard
Pros:
Comprehensive Security: WatchGuard offers a unified approach, simplifying the deployment and management of various security products and services.
Clarity & Control: The WatchGuard Cloud provides centralized security administration, enhanced visibility, and advanced reporting capabilities.
Shared Knowledge: Integrated knowledge-sharing capabilities enable a true XDR-based security strategy and a zero trust, identity-based security posture.
Cons:
Complexity for Small Businesses: Advanced features may overwhelm small businesses with limited IT resources.
Cost: Enterprise-grade, AI-enabled network detection and response capabilities can be costly for smaller organizations.
Dependency on Cloud: Heavy reliance on cloud-based management may not suit organizations with strict data residency requirements.
6. Palo Alto Networks

Palo Alto Networks offers advanced cybersecurity solutions designed to protect businesses from modern threats. Utilizing AI-driven technology, their platform provides comprehensive security across networks, clouds, and endpoints. With a focus on simplicity and efficiency, Palo Alto Networks aims to deliver robust protection while streamlining security operations for organizations of all sizes.
Palo Alto Networks Pricing
Palo Alto Networks' pricing is not public. Contact their support for more info.
Palo Alto Networks Reviews
Palo Alto Networks has an overall rating of 4.4 out of 5 stars based on 208 reviews. Users appreciate its robust security and ease of use. Check out more of our reviews here!
Pros and Cons of Palo Alto Networks
Pros:
AI-Powered Security: Precision AI enhances threat detection and remediation, providing proactive protection against sophisticated cyber threats.
Comprehensive Solutions: Offers extensive security solutions for network, cloud, and security operations, ensuring robust defense mechanisms.
Industry Recognition: Recognized as a leader in multiple Gartner Magic Quadrants and Forrester Waves, showcasing its credibility and reliability.
Cons:
Complexity: The wide range of products and services can be overwhelming for users, requiring significant time to navigate and implement effectively.
Cost: High-end security solutions and services can be expensive, potentially limiting accessibility for smaller organizations with tight budgets.
Learning Curve: Advanced features and AI-driven solutions may require significant training and expertise, posing a challenge for new users.
7. ClearVPN

ClearVPN is a user-friendly VPN service designed to enhance online privacy and security. With a focus on simplicity and powerful technology, ClearVPN offers seamless connectivity and optimal performance for various online activities, ensuring a hassle-free experience for users of all technical levels.
ClearVPN Pricing
1 Month Plan: $9.99 per month
1 Year Plan: $3.75 per month, billed annually at $44.99
ClearVPN Reviews
ClearVPN has an overall rating of 4.3 out of 5 stars based on 10 reviews. Users appreciate its ease of use and fast speeds. Check out more of our reviews here!
Pros and Cons of ClearVPN
Pros:
Ease of Use: ClearVPN's one-tap interface simplifies the process, making it accessible for all users.
Enhanced Security: High-level encryption and advanced VPN protocols ensure robust user privacy and security.
Fast Servers: Optimized servers in over 45 countries provide excellent speed and performance.
Cons:
Limited Compatibility: The Mac version does not support older operating systems, limiting its usability.
Interface Inconsistencies: Different interfaces across devices may confuse users switching between them.
Subscription Requirement: Full features and benefits are locked behind a premium subscription.
8. Todyl

Todyl is a cybersecurity platform offering a modular and comprehensive approach to security. Designed for ease of use and scalability, Todyl consolidates multiple security capabilities into a single-agent platform, making it ideal for businesses of all sizes. It ensures robust protection while simplifying deployment and management.
Todyl Pricing
Todyl's pricing is not public. Contact their support for more info.
Todyl Reviews
Todyl has an overall rating of 4.7 out of 5 stars based on 41 reviews. Users appreciate its ease of use and customer support. Check out more of our reviews here!
Pros and Cons of Todyl
Pros:
Comprehensive Security: Todyl offers a consolidated, customizable cybersecurity platform, ensuring robust protection across various modules.
Ease of Use: Simplifies management and deployment, making it accessible for IT teams to own and operate cybersecurity effectively.
Customer Support: Highly praised by users for responsive and helpful support, enhancing overall user experience.
Cons:
Technical Issues: Some users report occasional technical problems, affecting the platform's reliability.
Integration Issues: Challenges with integrating Todyl with existing systems have been noted by several users.
Pricing Concerns: The cost of Todyl's comprehensive solutions can be a barrier for smaller organizations.
9. SaferVPN

SaferVPN is a user-friendly VPN service designed to enhance online privacy and security. It offers fast speeds, strong encryption, and a no-logs policy, ensuring a secure and private browsing experience. With support for multiple devices, SaferVPN aims to provide reliable and accessible protection for all users.
SaferVPN Pricing
1 Month Plan: $12.95 per month
1 Year Plan: $5.49 per month, billed annually at $65.88
3 Year Plan: $2.50 per month, billed $89.99 every 3 years
SaferVPN Reviews
SaferVPN has an overall rating of 4.3 out of 5 stars based on 60 reviews. Users appreciate its ease of use and strong security features. Check out more of our reviews here!
Pros and Cons of SaferVPN
Pros:
Ease of Use: SaferVPN's intuitive interface makes it accessible for users of all technical levels, ensuring a smooth and hassle-free experience.
Customer Support: Responsive and helpful customer support enhances user satisfaction, providing timely assistance and resolving issues efficiently.
Privacy Protection: Strong encryption and a strict no-logs policy ensure that user data remains private and secure, safeguarding online activities.
Cons:
Slow Speed: Some users report slower connection speeds, which can affect streaming and downloading activities.
Expensive: The cost of SaferVPN's plans may be a barrier for budget-conscious users, especially when compared to competitors.
Limited Location Options: Despite a decent server variety, some regions have fewer server options, limiting flexibility for users in those areas.
10. Proton VPN

Proton VPN is a secure, fast VPN service designed to protect user privacy and provide unrestricted internet access. Based in Switzerland, it ensures strong privacy protections and a strict no-logs policy. Proton VPN offers seamless connectivity and optimal performance for various online activities, making it user-friendly and reliable.
Proton VPN Pricing
1-month plan: $9.99/month
1-year plan: $4.99/month (billed $59.88 annually)
2-year plan: $4.49/month (billed $107.76 biennially)
Proton Free: Free forever
Proton VPN Reviews
Proton VPN has an overall rating of 4.0 out of 5 stars based on 2 reviews. Users appreciate its robust security features and strong encryption. Check out more of our reviews here!
Pros and Cons of Proton VPN
Pros:
Swiss-based: Proton VPN is headquartered in Switzerland, ensuring strong privacy laws and protection from EU and US jurisdiction.
Strict no-logs policy: Proton VPN does not track or record user activity, ensuring complete privacy.
Multi-platform support: Available on Windows, macOS, Linux, Chromebook, Android, Android TV, and iOS/iPadOS, offering flexibility.
Cons:
Speed on Free Plan: The free version may not offer the same speed and features as the paid plans, affecting performance.
Limited Free Servers: The free version has limited server options compared to the paid plans, restricting choices.
Cost of Paid Plans: Users seeking faster speeds and more features need to subscribe to a paid plan, which can be costly.
Looking to secure your technical infrastructure?
Twingate offers granular access controls and deployment automations to protect your VPC environment. By leveraging Zero Trust security tools, Twingate ensures that private resources and internet traffic remain secure, making it an ideal solution for modern businesses. Try Twingate for Free today!
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
The Best 10 Alternatives to UH VPN (+ Pricing & Reviews)
Twingate Team
•
•
Jul 27, 2024

UH VPN is a secure, fast, and easy-to-use VPN platform designed to enhance online privacy and security. It offers features like enhanced security, simple profile distribution, and per-device revocation. However, UH VPN might not be the choice for everyone. This article explores the benefits and limitations of UH VPN.

10 Alternatives to UH VPN
1. Twingate

Twingate is a network security solution designed to replace traditional VPNs for remote access, offering a zero-trust security model and seamless deployment alongside existing infrastructure. With a focus on ease of use and scalability, Twingate aims to provide a secure and maintainable solution for businesses of all sizes.
Twingate Pricing
Starter: Free per user/month
Teams: $6 per user/month (monthly), $5 per user/month (yearly)
Business: $12 per user/month (monthly), $10 per user/month (yearly)
Enterprise: Custom pricing per user/month
Twingate Reviews
Twingate has an overall rating of 4.7 out of 5 stars based on 63 reviews. Users praise its ease of setup and high security. Check out more of our reviews here!
Pros and Cons of Twingate
Pros:
Enhanced Security: Twingate's zero trust model ensures that only authenticated users can access specific resources, significantly reducing the risk of unauthorized access.
Ease of Deployment: Setting up Twingate is straightforward and quick, allowing businesses to implement it without extensive technical expertise or prolonged downtime.
High Performance: Users consistently report that Twingate offers faster and more reliable connections compared to traditional VPN solutions, enhancing overall productivity.
Cons:
Initial Learning Curve: Some users may find the initial setup and understanding of zero trust principles challenging, especially if they are new to this security model.
Internet Dependency: As a cloud-based solution, Twingate's performance is reliant on stable internet connectivity, which can be a limitation in areas with poor internet service.
Limited Customization: While Twingate offers robust features, some users have noted that the platform lacks certain customization options that might be necessary for specific use cases.
2. Zscaler

Zscaler is a cybersecurity solution that replaces traditional VPNs with a zero-trust model, ensuring secure access to applications and data. It offers seamless deployment and scalability, making it ideal for businesses of all sizes. Zscaler focuses on securing users, cloud workloads, and IoT/OT devices.
Zscaler Pricing
Zscaler's pricing is not public. Contact their support for more info.
Zscaler Reviews
Zscaler has an overall rating of 4.5 out of 5 stars based on 43 reviews. Users praise its robust security and ease of use. Check out more of our reviews here!
Pros and Cons ofZscaler
Pros:
Comprehensive Security: Zscaler offers extensive security solutions, including cyberthreat protection and data protection, ensuring robust defense mechanisms.
Zero Trust Architecture: Provides zero trust connectivity for users, workloads, IoT/OT devices, and B2B applications, enhancing overall security.
Recognition and Trust: Recognized as a leader in the Gartner Magic Quadrant for Security Service Edge (SSE), trusted by 35% of Global 2000 companies.
Cons:
Complexity for New Users: The extensive range of products and solutions might be overwhelming for new users or smaller organizations.
Dependency on Cloud: Heavy reliance on cloud infrastructure, which may not be suitable for all organizations, especially those with strict data residency requirements.
Cost Considerations: Potentially high costs associated with comprehensive security solutions and zero trust architecture, which might be a barrier for smaller enterprises.
3. Azure VPN Gateway

Azure VPN Gateway is a service that allows users to securely connect to the cloud. It offers seamless integration with existing infrastructure and supports various account options, including free and pay-as-you-go plans. Designed for scalability and ease of use, it aims to provide secure and reliable cloud connectivity for businesses.
Azure VPN Gateway Pricing
Azure Free Account: $200 credit for 30 days
Pay as You Go: Pay only for what you use
Azure VPN Gateway Reviews
Azure VPN Gateway has an overall rating of 4.1 out of 5 stars based on 21 reviews. Users appreciate its reliability and security. Check out more of our reviews here!
Pros and Cons of Azure VPN Gateway
Pros:
Secure Connection: Ensures secure connections to the cloud using industry-standard protocols like IPsec and IKE.
Ease of Setup: Many users find Azure VPN Gateway easy to set up and configure, reducing deployment time.
Reliability: Users appreciate the reliability and minimal downtime, ensuring consistent access to resources.
Cons:
Certificate Generation: The process of generating certificates can be cumbersome and is considered outdated by some users.
Cost: While there are free options, extensive use beyond the free tier can incur significant costs.
Implementation Time: It can take time to implement, which might be a drawback for some users.
4. CyberGhost

CyberGhost VPN is a service designed to ensure online privacy and security. It offers strong encryption, a no-logs policy, and fast speeds across a large server fleet. With support for multiple devices and 24/7 customer service, CyberGhost aims to provide a reliable and user-friendly VPN experience.
CyberGhost Pricing
1 Month Plan: $12.99 per month
28 Month Plan: $2.03 per month, billed $56.94 for the first 2 years and yearly thereafter
6 Month Plan: $6.99 per month, billed $41.94 every 6 months
CyberGhost Reviews
CyberGhost has an overall rating of 4.5 out of 5 stars based on 20 reviews. Users praise its wide array of server locations. Check out more of our reviews here!
Pros and Cons of CyberGhost
Pros:
Complete Privacy: CyberGhost's no-logs policy and strong encryption ensure your online activities remain private and secure.
Device Compatibility: Supports up to 7 devices simultaneously, making it ideal for families or small teams.
Large Server Fleet: Access to servers in 100 countries, providing extensive global coverage and flexibility.
Cons:
Access Issues: Some users report occasional difficulties accessing certain websites or services.
Limited Location Options: Despite a large server fleet, some regions may have fewer server options.
Connectivity Issues: Users have experienced intermittent connectivity problems, affecting the reliability of the service.
5. Watchguard

WatchGuard provides comprehensive cybersecurity solutions designed to protect businesses of all sizes. With features like AI-driven network detection, unified security platforms, and 24/7 managed detection and response, WatchGuard aims to deliver robust, scalable, and user-friendly security solutions for modern enterprises.
Watchguard Pricing
Watchguard's pricing is not public. Contact their support for more info.
Watchguard Reviews
WatchGuard has an overall rating of 4.7 out of 5 stars based on 258 reviews. Users appreciate its ease of use and strong security features. Check out more of our reviews here!
Pros and Cons of Watchguard
Pros:
Comprehensive Security: WatchGuard offers a unified approach, simplifying the deployment and management of various security products and services.
Clarity & Control: The WatchGuard Cloud provides centralized security administration, enhanced visibility, and advanced reporting capabilities.
Shared Knowledge: Integrated knowledge-sharing capabilities enable a true XDR-based security strategy and a zero trust, identity-based security posture.
Cons:
Complexity for Small Businesses: Advanced features may overwhelm small businesses with limited IT resources.
Cost: Enterprise-grade, AI-enabled network detection and response capabilities can be costly for smaller organizations.
Dependency on Cloud: Heavy reliance on cloud-based management may not suit organizations with strict data residency requirements.
6. Palo Alto Networks

Palo Alto Networks offers advanced cybersecurity solutions designed to protect businesses from modern threats. Utilizing AI-driven technology, their platform provides comprehensive security across networks, clouds, and endpoints. With a focus on simplicity and efficiency, Palo Alto Networks aims to deliver robust protection while streamlining security operations for organizations of all sizes.
Palo Alto Networks Pricing
Palo Alto Networks' pricing is not public. Contact their support for more info.
Palo Alto Networks Reviews
Palo Alto Networks has an overall rating of 4.4 out of 5 stars based on 208 reviews. Users appreciate its robust security and ease of use. Check out more of our reviews here!
Pros and Cons of Palo Alto Networks
Pros:
AI-Powered Security: Precision AI enhances threat detection and remediation, providing proactive protection against sophisticated cyber threats.
Comprehensive Solutions: Offers extensive security solutions for network, cloud, and security operations, ensuring robust defense mechanisms.
Industry Recognition: Recognized as a leader in multiple Gartner Magic Quadrants and Forrester Waves, showcasing its credibility and reliability.
Cons:
Complexity: The wide range of products and services can be overwhelming for users, requiring significant time to navigate and implement effectively.
Cost: High-end security solutions and services can be expensive, potentially limiting accessibility for smaller organizations with tight budgets.
Learning Curve: Advanced features and AI-driven solutions may require significant training and expertise, posing a challenge for new users.
7. ClearVPN

ClearVPN is a user-friendly VPN service designed to enhance online privacy and security. With a focus on simplicity and powerful technology, ClearVPN offers seamless connectivity and optimal performance for various online activities, ensuring a hassle-free experience for users of all technical levels.
ClearVPN Pricing
1 Month Plan: $9.99 per month
1 Year Plan: $3.75 per month, billed annually at $44.99
ClearVPN Reviews
ClearVPN has an overall rating of 4.3 out of 5 stars based on 10 reviews. Users appreciate its ease of use and fast speeds. Check out more of our reviews here!
Pros and Cons of ClearVPN
Pros:
Ease of Use: ClearVPN's one-tap interface simplifies the process, making it accessible for all users.
Enhanced Security: High-level encryption and advanced VPN protocols ensure robust user privacy and security.
Fast Servers: Optimized servers in over 45 countries provide excellent speed and performance.
Cons:
Limited Compatibility: The Mac version does not support older operating systems, limiting its usability.
Interface Inconsistencies: Different interfaces across devices may confuse users switching between them.
Subscription Requirement: Full features and benefits are locked behind a premium subscription.
8. Todyl

Todyl is a cybersecurity platform offering a modular and comprehensive approach to security. Designed for ease of use and scalability, Todyl consolidates multiple security capabilities into a single-agent platform, making it ideal for businesses of all sizes. It ensures robust protection while simplifying deployment and management.
Todyl Pricing
Todyl's pricing is not public. Contact their support for more info.
Todyl Reviews
Todyl has an overall rating of 4.7 out of 5 stars based on 41 reviews. Users appreciate its ease of use and customer support. Check out more of our reviews here!
Pros and Cons of Todyl
Pros:
Comprehensive Security: Todyl offers a consolidated, customizable cybersecurity platform, ensuring robust protection across various modules.
Ease of Use: Simplifies management and deployment, making it accessible for IT teams to own and operate cybersecurity effectively.
Customer Support: Highly praised by users for responsive and helpful support, enhancing overall user experience.
Cons:
Technical Issues: Some users report occasional technical problems, affecting the platform's reliability.
Integration Issues: Challenges with integrating Todyl with existing systems have been noted by several users.
Pricing Concerns: The cost of Todyl's comprehensive solutions can be a barrier for smaller organizations.
9. SaferVPN

SaferVPN is a user-friendly VPN service designed to enhance online privacy and security. It offers fast speeds, strong encryption, and a no-logs policy, ensuring a secure and private browsing experience. With support for multiple devices, SaferVPN aims to provide reliable and accessible protection for all users.
SaferVPN Pricing
1 Month Plan: $12.95 per month
1 Year Plan: $5.49 per month, billed annually at $65.88
3 Year Plan: $2.50 per month, billed $89.99 every 3 years
SaferVPN Reviews
SaferVPN has an overall rating of 4.3 out of 5 stars based on 60 reviews. Users appreciate its ease of use and strong security features. Check out more of our reviews here!
Pros and Cons of SaferVPN
Pros:
Ease of Use: SaferVPN's intuitive interface makes it accessible for users of all technical levels, ensuring a smooth and hassle-free experience.
Customer Support: Responsive and helpful customer support enhances user satisfaction, providing timely assistance and resolving issues efficiently.
Privacy Protection: Strong encryption and a strict no-logs policy ensure that user data remains private and secure, safeguarding online activities.
Cons:
Slow Speed: Some users report slower connection speeds, which can affect streaming and downloading activities.
Expensive: The cost of SaferVPN's plans may be a barrier for budget-conscious users, especially when compared to competitors.
Limited Location Options: Despite a decent server variety, some regions have fewer server options, limiting flexibility for users in those areas.
10. Proton VPN

Proton VPN is a secure, fast VPN service designed to protect user privacy and provide unrestricted internet access. Based in Switzerland, it ensures strong privacy protections and a strict no-logs policy. Proton VPN offers seamless connectivity and optimal performance for various online activities, making it user-friendly and reliable.
Proton VPN Pricing
1-month plan: $9.99/month
1-year plan: $4.99/month (billed $59.88 annually)
2-year plan: $4.49/month (billed $107.76 biennially)
Proton Free: Free forever
Proton VPN Reviews
Proton VPN has an overall rating of 4.0 out of 5 stars based on 2 reviews. Users appreciate its robust security features and strong encryption. Check out more of our reviews here!
Pros and Cons of Proton VPN
Pros:
Swiss-based: Proton VPN is headquartered in Switzerland, ensuring strong privacy laws and protection from EU and US jurisdiction.
Strict no-logs policy: Proton VPN does not track or record user activity, ensuring complete privacy.
Multi-platform support: Available on Windows, macOS, Linux, Chromebook, Android, Android TV, and iOS/iPadOS, offering flexibility.
Cons:
Speed on Free Plan: The free version may not offer the same speed and features as the paid plans, affecting performance.
Limited Free Servers: The free version has limited server options compared to the paid plans, restricting choices.
Cost of Paid Plans: Users seeking faster speeds and more features need to subscribe to a paid plan, which can be costly.
Looking to secure your technical infrastructure?
Twingate offers granular access controls and deployment automations to protect your VPC environment. By leveraging Zero Trust security tools, Twingate ensures that private resources and internet traffic remain secure, making it an ideal solution for modern businesses. Try Twingate for Free today!
Solutions
Solutions
The VPN replacement your workforce will love.
Solutions