Announcing WebAuthn for Twingate Universal MFA
Emily Lehman
•
Feb 13, 2023
Twingate is excited to announce the launch of our support for WebAuthn, signaling the first step in laying the foundation for a passwordless future. With this new functionality, Twingate customers can leverage additional types of authentication – including biometrics and Yubikeys – when using Twingate’s Universal MFA for SSH, RDP, or legacy applications that don’t natively support MFA.
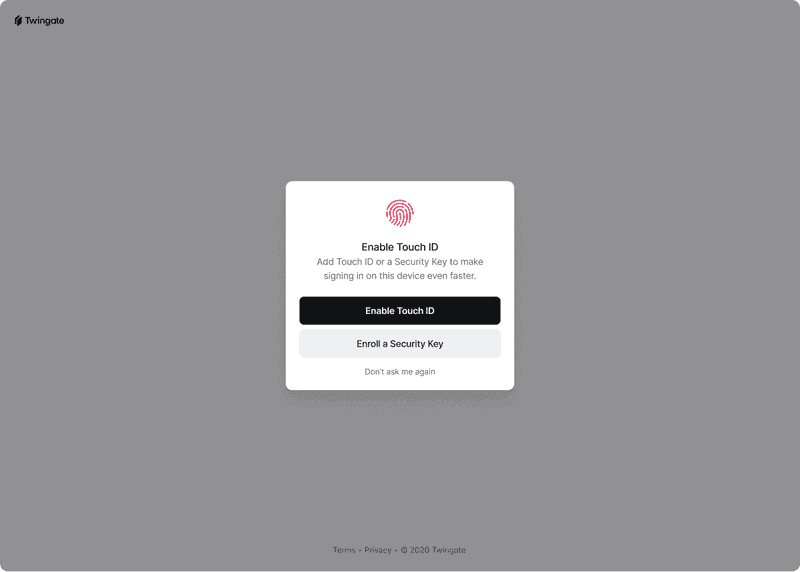
To enable WebAuthn for Twingate, customers just need to enable MFA as a Security Policy requirement for a Twingate-protected Resource - that’s it. End users will then be prompted to configure a WebAuthn method as a part of the standard MFA workflow when attempting to access the Resource. Admins can then review which authentication methods are configured on a user’s profile within the Admin Console.
The problem with passwords
It’s become a cliche to say it’s “more important than ever‚ for organizations to improve their approaches to cybersecurity, but it’s a cliche because it’s true: cyberattacks continue to surge year-over-year, and legacy security models don’t address the new challenges presented by an increasingly distributed global workforce.
We all know that passwords alone are simply not secure enough. They can be stolen, leaked, or unwittingly shared via phishing and social engineering attempts from hackers. These vulnerabilities are compounded by human behavior: up to 65% of people admit to reusing passwords, and 45% do not consider password reuse to be a serious issue.
Multi-factor authentication is one step forward in improving security by providing an additional layer of authentication, but it’s not infallible. The majority of MFA workflows still rely on one-time passwords (OTPs), and while certainly more secure than passwords alone, OTPs remain vulnerable to phishing attacks. Reverse proxy tools like Modlishka and Evilginx2 can capture both credentials and the authentication tokens sent as cookies, allowing hackers to bypass 2FA.
So what can organizations do to combat these security weaknesses? Enter: WebAuthn.
What is WebAuthn?
WebAuthn is the shortened name for Web Authentication API, a specification written by the W3C and FIDO, that allows servers to register and authenticate users using public key cryptography instead of a password.
A WebAuthn registration workflow generates a private-public keypair once the user provides a strong authenticator - think a fingerprint or a YubiKey. The private key is stored securely on the user’s device while the randomly generated public key is sent to the server for storage (you can read more about how WebAuthn works under the hood in this blog post).
This approach relies on authenticators that are both stronger and easier to use than passwords, leading to a number of security benefits:
Eliminate man-in-the-middle attacks: Authentication requests can’t be captured and successfully replayed, preventing hackers from using authentication tokens sent as cookies to bypass MFA.
Reduce incentive to hack databases: Only public keys are stored on servers, but they are effectively useless without the corresponding private key. Theoretically, this makes databases less attractive to hackers since the public keys aren’t useful on their own.
Improve end-user experience: The more friction involved in a security workflow, the more people will try to get around it. By leveraging authentication methods that are actually easier for end-users, organizations can ensure that their employees don’t try to work around their security procedures.
It seems like the perfect solution to the world’s cybersecurity woes - both more secure and easier to use – so why isn’t WebAuthn more widely adopted?
The simple answer is that WebAuthn gets very complicated very quickly (at least for application developers). WebAuthn is not browser agnostic, meaning product teams must explicitly build support for not just all browsers, but their various versions. Add to this the combinations of platforms and authenticators that need to be supported, and you quickly get a complex matrix of compatibilities that need to be accounted for.
This complexity means that despite widespread acceptance of its security superiority, WebAuthn is not as widely supported or adopted as you might expect.
Zero Trust Made Easy
A core tenet here at Twingate is making Zero Trust principles as easy to adopt as possible for both administrators and for end users.
Strong identity verification is a key component of a Zero Trust security model, but organizations often struggle to implement strident authentication policies across their entire ecosystem due to lack of functionality, heavy configuration requirements, and ongoing maintenance from already resource-strapped teams.
Twingate makes it easy to implement MFA for historically unsupported workflows like SSH-ing, RDP-ing, and accessing legacy applications. Twingate’s support for WebAuthn deepens the strength of these authentication methods while reducing friction in the end-user experience.
You can find full details on Twingate’s Universal MFA on our documents page. Not a Twingate customer yet? If you’re interested in taking Twingate for a spin, you can request a personalized demo from our team or try it out yourself for free.
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Announcing WebAuthn for Twingate Universal MFA
Emily Lehman
•
Feb 13, 2023

Twingate is excited to announce the launch of our support for WebAuthn, signaling the first step in laying the foundation for a passwordless future. With this new functionality, Twingate customers can leverage additional types of authentication – including biometrics and Yubikeys – when using Twingate’s Universal MFA for SSH, RDP, or legacy applications that don’t natively support MFA.
To enable WebAuthn for Twingate, customers just need to enable MFA as a Security Policy requirement for a Twingate-protected Resource - that’s it. End users will then be prompted to configure a WebAuthn method as a part of the standard MFA workflow when attempting to access the Resource. Admins can then review which authentication methods are configured on a user’s profile within the Admin Console.

The problem with passwords
It’s become a cliche to say it’s “more important than ever‚ for organizations to improve their approaches to cybersecurity, but it’s a cliche because it’s true: cyberattacks continue to surge year-over-year, and legacy security models don’t address the new challenges presented by an increasingly distributed global workforce.
We all know that passwords alone are simply not secure enough. They can be stolen, leaked, or unwittingly shared via phishing and social engineering attempts from hackers. These vulnerabilities are compounded by human behavior: up to 65% of people admit to reusing passwords, and 45% do not consider password reuse to be a serious issue.
Multi-factor authentication is one step forward in improving security by providing an additional layer of authentication, but it’s not infallible. The majority of MFA workflows still rely on one-time passwords (OTPs), and while certainly more secure than passwords alone, OTPs remain vulnerable to phishing attacks. Reverse proxy tools like Modlishka and Evilginx2 can capture both credentials and the authentication tokens sent as cookies, allowing hackers to bypass 2FA.
So what can organizations do to combat these security weaknesses? Enter: WebAuthn.
What is WebAuthn?
WebAuthn is the shortened name for Web Authentication API, a specification written by the W3C and FIDO, that allows servers to register and authenticate users using public key cryptography instead of a password.
A WebAuthn registration workflow generates a private-public keypair once the user provides a strong authenticator - think a fingerprint or a YubiKey. The private key is stored securely on the user’s device while the randomly generated public key is sent to the server for storage (you can read more about how WebAuthn works under the hood in this blog post).
This approach relies on authenticators that are both stronger and easier to use than passwords, leading to a number of security benefits:
Eliminate man-in-the-middle attacks: Authentication requests can’t be captured and successfully replayed, preventing hackers from using authentication tokens sent as cookies to bypass MFA.
Reduce incentive to hack databases: Only public keys are stored on servers, but they are effectively useless without the corresponding private key. Theoretically, this makes databases less attractive to hackers since the public keys aren’t useful on their own.
Improve end-user experience: The more friction involved in a security workflow, the more people will try to get around it. By leveraging authentication methods that are actually easier for end-users, organizations can ensure that their employees don’t try to work around their security procedures.
It seems like the perfect solution to the world’s cybersecurity woes - both more secure and easier to use – so why isn’t WebAuthn more widely adopted?
The simple answer is that WebAuthn gets very complicated very quickly (at least for application developers). WebAuthn is not browser agnostic, meaning product teams must explicitly build support for not just all browsers, but their various versions. Add to this the combinations of platforms and authenticators that need to be supported, and you quickly get a complex matrix of compatibilities that need to be accounted for.
This complexity means that despite widespread acceptance of its security superiority, WebAuthn is not as widely supported or adopted as you might expect.
Zero Trust Made Easy
A core tenet here at Twingate is making Zero Trust principles as easy to adopt as possible for both administrators and for end users.
Strong identity verification is a key component of a Zero Trust security model, but organizations often struggle to implement strident authentication policies across their entire ecosystem due to lack of functionality, heavy configuration requirements, and ongoing maintenance from already resource-strapped teams.
Twingate makes it easy to implement MFA for historically unsupported workflows like SSH-ing, RDP-ing, and accessing legacy applications. Twingate’s support for WebAuthn deepens the strength of these authentication methods while reducing friction in the end-user experience.
You can find full details on Twingate’s Universal MFA on our documents page. Not a Twingate customer yet? If you’re interested in taking Twingate for a spin, you can request a personalized demo from our team or try it out yourself for free.
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Announcing WebAuthn for Twingate Universal MFA
Emily Lehman
•
Feb 13, 2023

Twingate is excited to announce the launch of our support for WebAuthn, signaling the first step in laying the foundation for a passwordless future. With this new functionality, Twingate customers can leverage additional types of authentication – including biometrics and Yubikeys – when using Twingate’s Universal MFA for SSH, RDP, or legacy applications that don’t natively support MFA.
To enable WebAuthn for Twingate, customers just need to enable MFA as a Security Policy requirement for a Twingate-protected Resource - that’s it. End users will then be prompted to configure a WebAuthn method as a part of the standard MFA workflow when attempting to access the Resource. Admins can then review which authentication methods are configured on a user’s profile within the Admin Console.

The problem with passwords
It’s become a cliche to say it’s “more important than ever‚ for organizations to improve their approaches to cybersecurity, but it’s a cliche because it’s true: cyberattacks continue to surge year-over-year, and legacy security models don’t address the new challenges presented by an increasingly distributed global workforce.
We all know that passwords alone are simply not secure enough. They can be stolen, leaked, or unwittingly shared via phishing and social engineering attempts from hackers. These vulnerabilities are compounded by human behavior: up to 65% of people admit to reusing passwords, and 45% do not consider password reuse to be a serious issue.
Multi-factor authentication is one step forward in improving security by providing an additional layer of authentication, but it’s not infallible. The majority of MFA workflows still rely on one-time passwords (OTPs), and while certainly more secure than passwords alone, OTPs remain vulnerable to phishing attacks. Reverse proxy tools like Modlishka and Evilginx2 can capture both credentials and the authentication tokens sent as cookies, allowing hackers to bypass 2FA.
So what can organizations do to combat these security weaknesses? Enter: WebAuthn.
What is WebAuthn?
WebAuthn is the shortened name for Web Authentication API, a specification written by the W3C and FIDO, that allows servers to register and authenticate users using public key cryptography instead of a password.
A WebAuthn registration workflow generates a private-public keypair once the user provides a strong authenticator - think a fingerprint or a YubiKey. The private key is stored securely on the user’s device while the randomly generated public key is sent to the server for storage (you can read more about how WebAuthn works under the hood in this blog post).
This approach relies on authenticators that are both stronger and easier to use than passwords, leading to a number of security benefits:
Eliminate man-in-the-middle attacks: Authentication requests can’t be captured and successfully replayed, preventing hackers from using authentication tokens sent as cookies to bypass MFA.
Reduce incentive to hack databases: Only public keys are stored on servers, but they are effectively useless without the corresponding private key. Theoretically, this makes databases less attractive to hackers since the public keys aren’t useful on their own.
Improve end-user experience: The more friction involved in a security workflow, the more people will try to get around it. By leveraging authentication methods that are actually easier for end-users, organizations can ensure that their employees don’t try to work around their security procedures.
It seems like the perfect solution to the world’s cybersecurity woes - both more secure and easier to use – so why isn’t WebAuthn more widely adopted?
The simple answer is that WebAuthn gets very complicated very quickly (at least for application developers). WebAuthn is not browser agnostic, meaning product teams must explicitly build support for not just all browsers, but their various versions. Add to this the combinations of platforms and authenticators that need to be supported, and you quickly get a complex matrix of compatibilities that need to be accounted for.
This complexity means that despite widespread acceptance of its security superiority, WebAuthn is not as widely supported or adopted as you might expect.
Zero Trust Made Easy
A core tenet here at Twingate is making Zero Trust principles as easy to adopt as possible for both administrators and for end users.
Strong identity verification is a key component of a Zero Trust security model, but organizations often struggle to implement strident authentication policies across their entire ecosystem due to lack of functionality, heavy configuration requirements, and ongoing maintenance from already resource-strapped teams.
Twingate makes it easy to implement MFA for historically unsupported workflows like SSH-ing, RDP-ing, and accessing legacy applications. Twingate’s support for WebAuthn deepens the strength of these authentication methods while reducing friction in the end-user experience.
You can find full details on Twingate’s Universal MFA on our documents page. Not a Twingate customer yet? If you’re interested in taking Twingate for a spin, you can request a personalized demo from our team or try it out yourself for free.
Solutions
Solutions
The VPN replacement your workforce will love.
Solutions